PROTECT
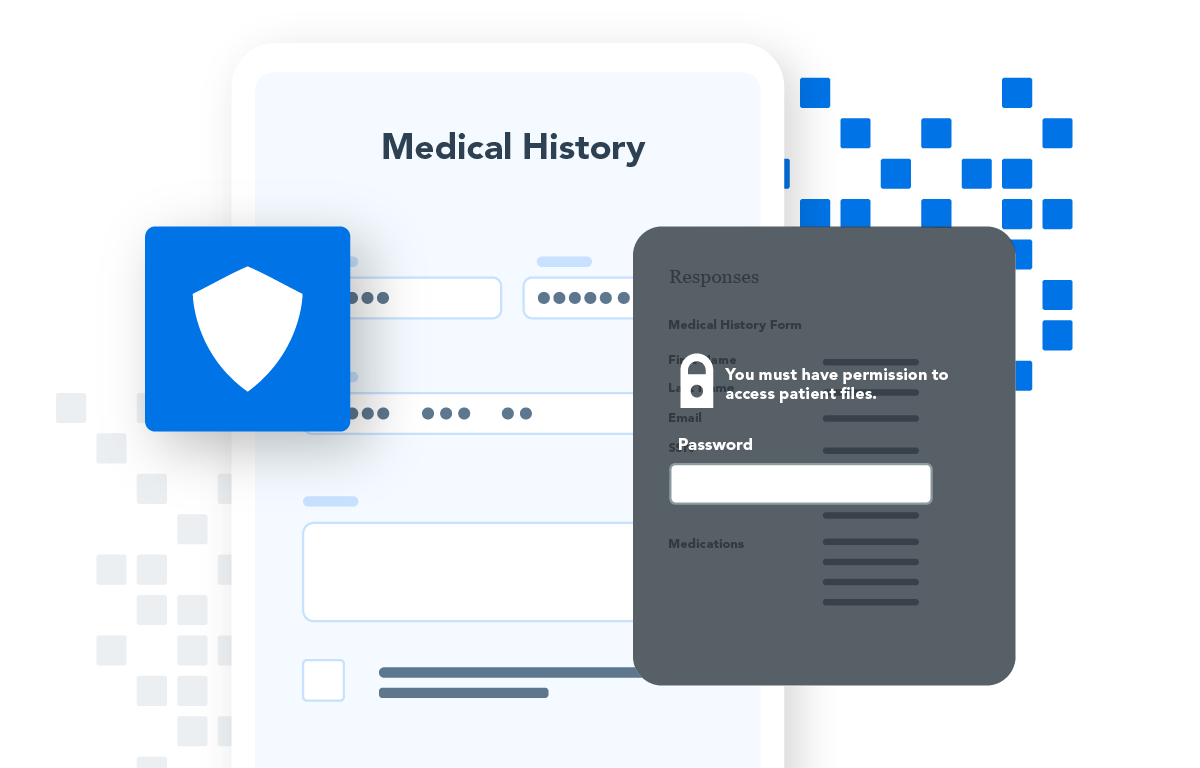
Safeguard Sensitive Data
Secure, fully compliant web forms
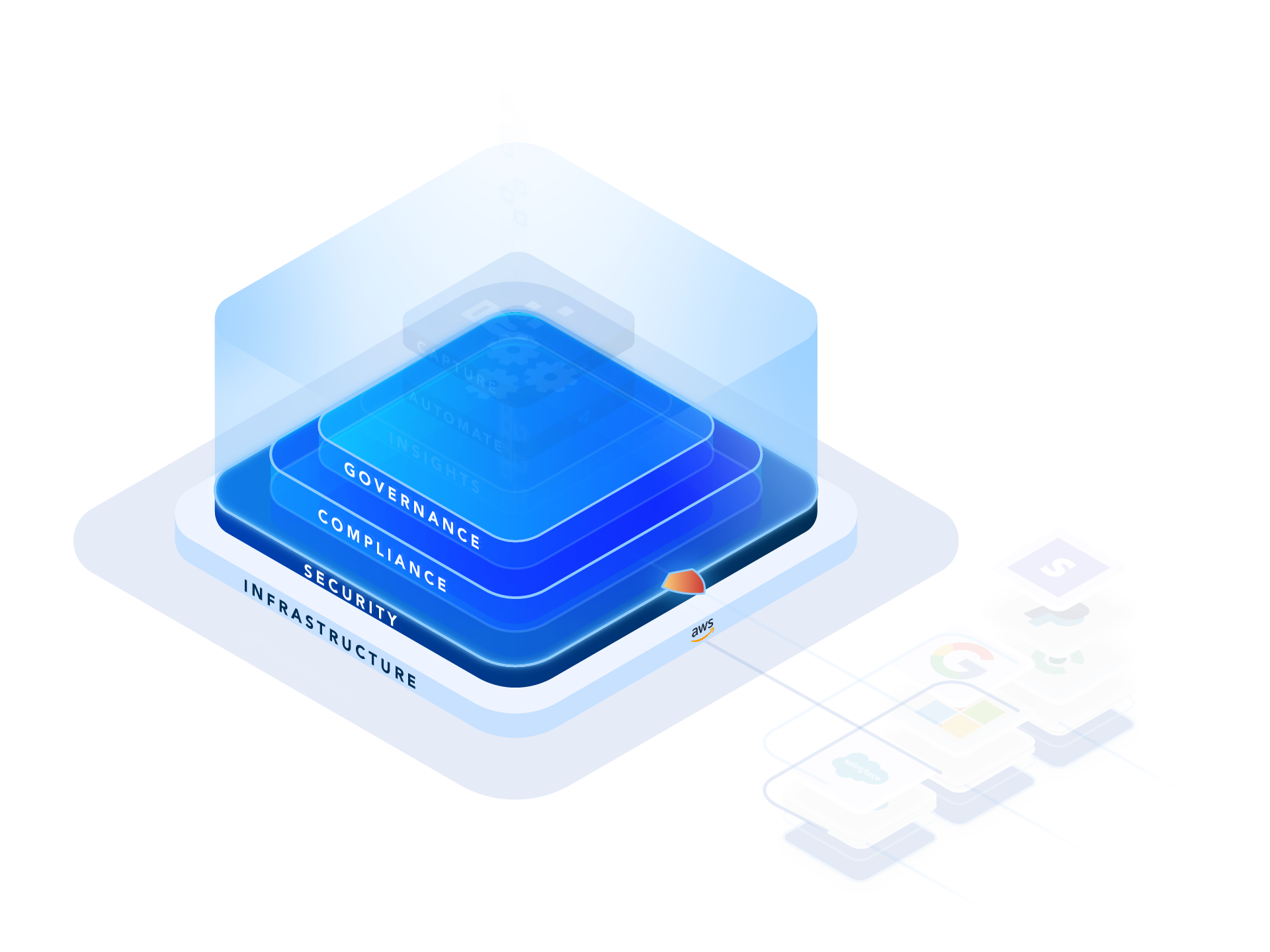
Best-in-class privacy, security, and compliance
The FormAssembly Data Collection Platform protects sensitive data—such as personal identification information, financial records, health information, and authentication data—while ensuring compliance and streamlining web forms and workflows.
With AWS’s world-class infrastructure and FormAssembly’s advanced web form security features, you can trust that we are as committed to protecting your data as you are.
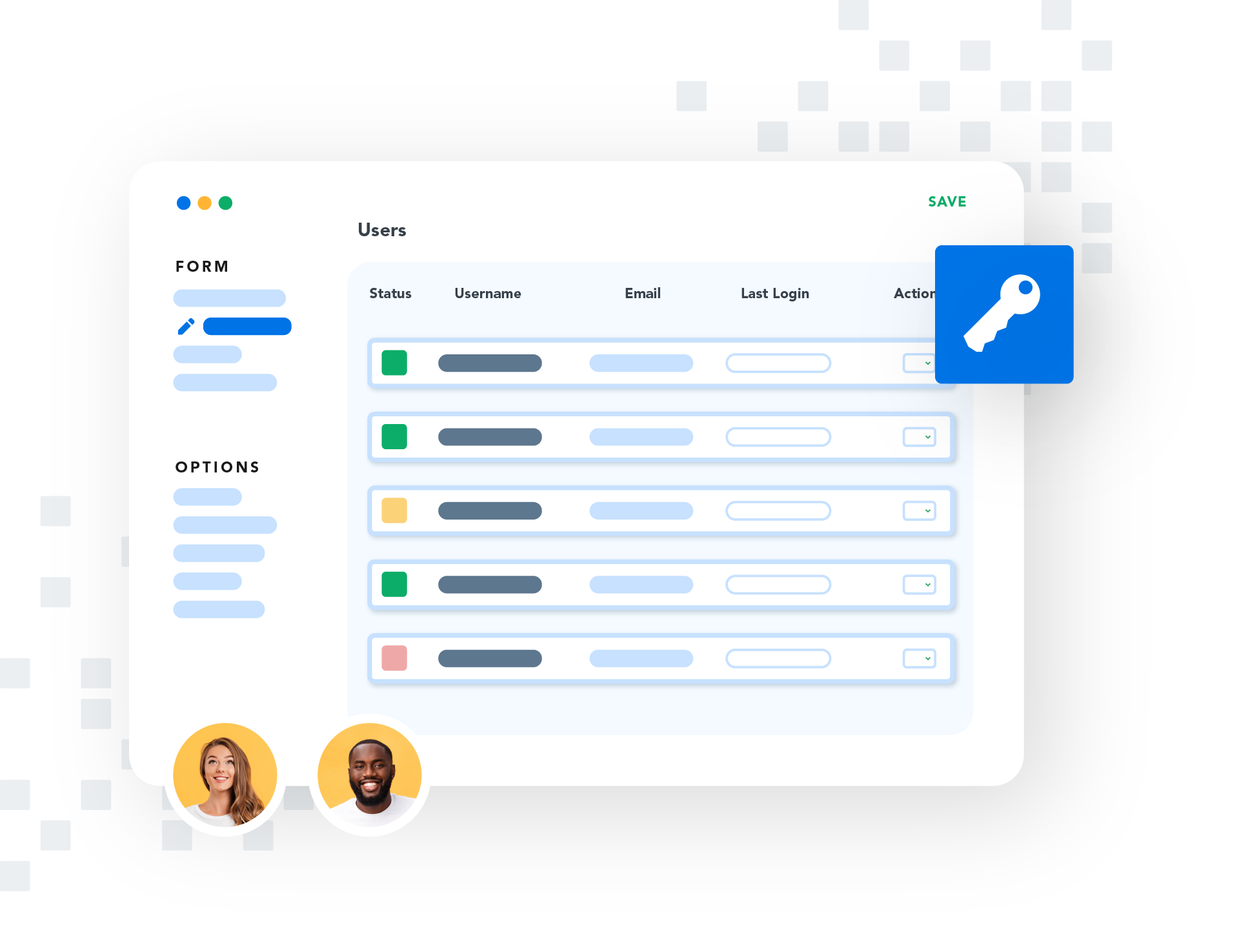
Gain visibility and control over data collection
The FormAssembly Data Collection Platform provides granular permissions, robust access controls, and audit capabilities that enable you to exercise authority and governance within your organization.
Data governance features
- Data privacy controls, access controls, and granular user permissions and licensing options
- User-defined data classification and retention policies
- Custom, automated data purge settings and audit logs
- CAS, LDAP, SAML identity authentication, and intelligent auto prefill

Is your data secure?
13 questions to ask before selecting a data collection provider. And insights into the answers you should expect.

Maintain compliance in data collection
The FormAssembly Data Collection Platform supports the most stringent compliance and regulatory requirements. From data localization to handling PHI, FormAssembly has you covered.
FormAssembly is compliant with:
- PCI-DSS
- HIPAA with BAA and available SLA
- GDPR
- CCPA
- FERPA
- SOC2 Type 2 Security Principle
- ISO 27001
- GLBA
- FedRAMP ready
- Accessibility and internationalization requirements

Always one step ahead with security
Start collecting your data securely today with a data collection solution that comes loaded with key security features, certifications, and operational standards to minimize risk, enhance privacy, and safeguard your business and customers.
FormAssembly security features:
- Data encryption in transit and at rest; TLS 1.2 and AES-256 safeguards for confidential data during transmission over public networks
- Data masking and obfuscation
- Secure file scan
- Users identity authentication with CAS, LDAP, and SAML
- Rigorous internal security standards including continuous monitoring, strict access control, employee training, and well-documented asset management practices

81% of organizations lack full visibility into their data collection systems
We asked CIOs and CISOs how they manage practices, policies, and risks in online data collection, and the results were surprising.